阿里雲內容分發網絡(Alibaba Cloud CDN)。無論您的業務是面向全球用戶的電商平台、新聞媒體、遊戲下載,還是企業官網,CDN都能顯著降低延遲、提高載入速度、節省源站頻寬並增強安全性。本教學將手把手指導您如何在阿里雲國際站完成CDN服務的開通與基礎設定。

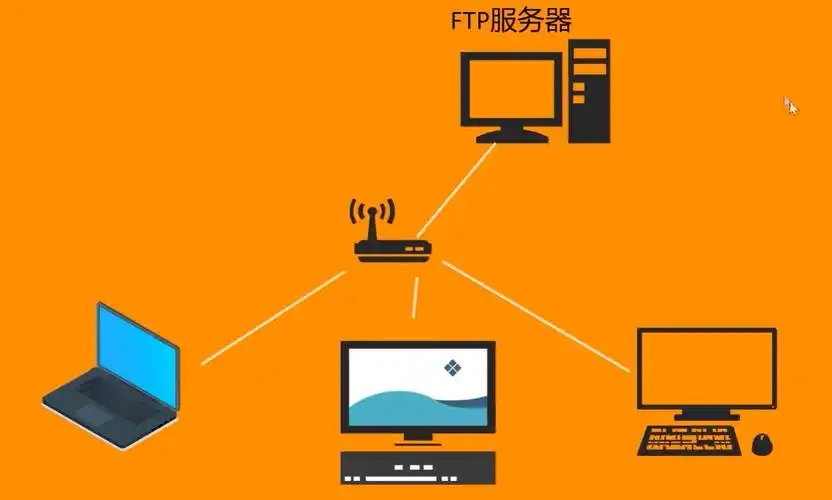
檔案傳輸協定(FTP)作為傳統的網路檔案共享方式,至今仍在許多應用場景中發揮重要作用。本文將詳細介紹如何在Linux環境下部署安全可靠的FTP檔案服務,採用業界廣泛認可的vsftpd服務軟體,幫助您快速建構高效能的檔案傳輸平台。
This article discusses the challenges and architectural patterns of implementing Model Context Protocol (MCP) services in enterprises, offering practi.

在數位化浪潮中,一個高效穩定的網站如同企業的「數位門面」。當我們談及自主建站,WordPress憑藉其41%的全球市佔率,始終是開發者的首選方案。但隨著雲端技術演進,「如何在雲伺服器實現企業級WordPress部署」已成為值得深究的課題。

在全球化數位浪潮加速演進的今天,雲端計算服務已成為跨國企業和全球開發者構建數位化業務的核心基礎設施。作為亞太地區領先的雲端服務提供商,阿里雲國際站(Alibaba Cloud International)透過遍佈全球的資料中心和豐富的雲端產品矩陣,為來自200多個國家和地區的企業及開發者提供穩定可靠的雲端服務。

This blog highlights the rise of cloud computing, Alibaba Cloud’s support for over 12,000 companies, and why cloud services are vital for future business success.

This article outlines a detailed strategy for designing and maintaining high-performance architectures on Alibaba Cloud.

This article starts from the business characteristics of user profiling, providing a comprehensive and multi-angle analysis of why Lindorm is a suitable choice for user profiling.

This article describes how to handle the preceding challenges based on event-driven architectures.

This blog explains how you can share your ACR registry across multiple Alibaba Cloud accounts.

This blog delves into the key challenges design companies face in today's fast-paced world and explore how Alibaba Cloud's EDS provides a comprehensive, secure, and flexible solution.

The article provides a technical overview of Alibaba Cloud's modern architecture, detailing its core components, performance metrics, and implementation strategies.

Three tier applications are a base for development of modern-day dynamic websites. It all started by having on premises servers hosting server-side scripts running on a database engine.

Di artikel sebelumnya kita membahas tentang bagaimana cara melakukan deployment mikrotik di Alibaba Cloud.

This article introduces three common types of master-worker architectures and discusses the challenges of preventing cascading failures in distributed systems.
This article explains the technologic details of the paper - PolarDB-MP: A Multi-Primary Cloud-Native Database via Disaggregated Shared Memory.

Unified batch and stream processing of Flink is a well-established concept in the stream computing field.
This article introduces how the new offline near real-time integrated architecture based on MaxCompute supports comprehensive business scenarios.

This article introduces the architecture and release notes of PolarDB-X V2.4 and the new clustered columnar index (CCI) feature in PolarDB-X v2.4.

This article analyzes the similarities and differences between PolarDB-X and DRDS from different perspectives.
