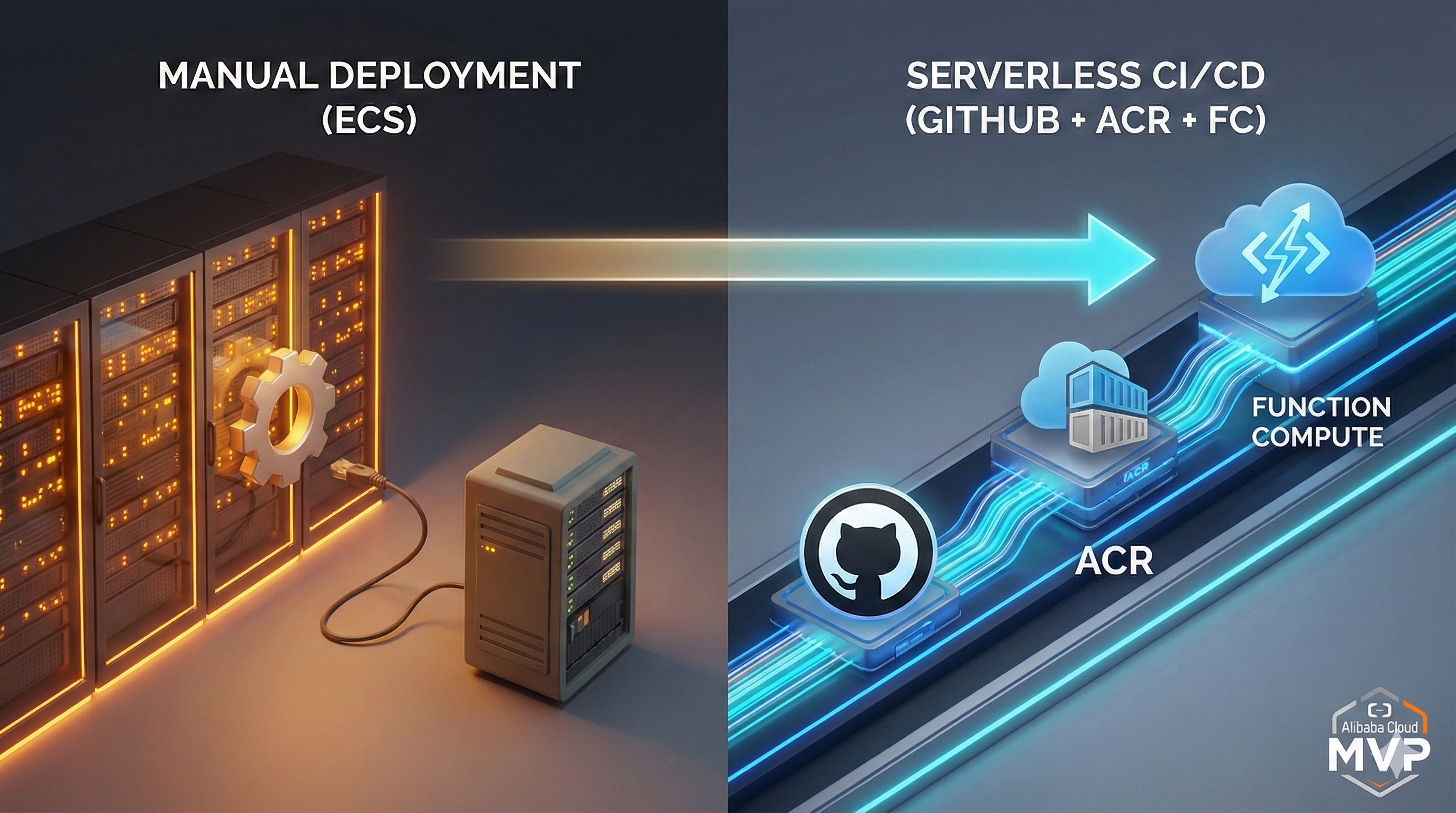
In the fast-paced world of software development, small teams (under 20 people) often struggle with the "infrastructure tax"—the significant time and c...
This guide outlines how to upgrade your database management strategy using the Database Autonomy Service (DAS) O&M Service.
This article introduces Alibaba Cloud's Vector Retrieval Service for Milvus, a fully managed, high-performance vector database that accelerates global...

This article introduces how financial organizations can achieve cost optimization and efficiency through cloud transformation to Alibaba Cloud by implementing FinOps practices.

Alibaba DAMO Academy has entered into a strategic collaboration with the International Telecommunication Union (ITU).

This article highlights the importance of CSPM on Alibaba Cloud for continuously assessing and enhancing cloud security to prevent breaches and ensure compliance.

阿里雲內容分發網絡(Alibaba Cloud CDN)。無論您的業務是面向全球用戶的電商平台、新聞媒體、遊戲下載,還是企業官網,CDN都能顯著降低延遲、提高載入速度、節省源站頻寬並增強安全性。本教學將手把手指導您如何在阿里雲國際站完成CDN服務的開通與基礎設定。

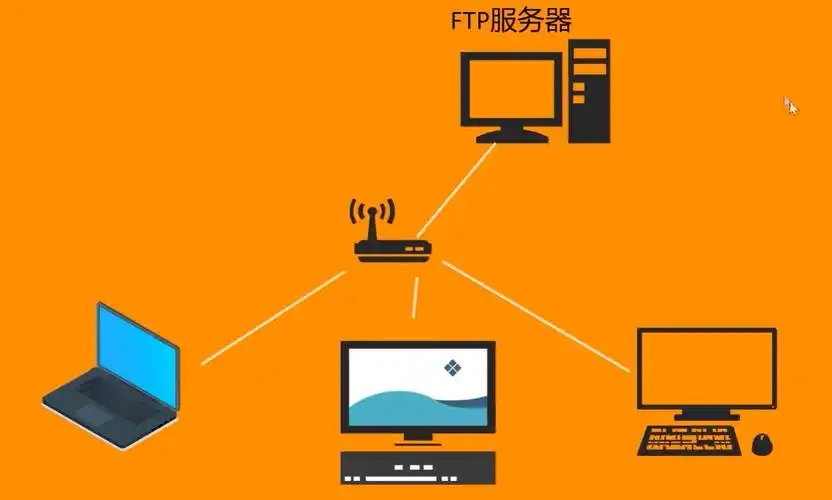
檔案傳輸協定(FTP)作為傳統的網路檔案共享方式,至今仍在許多應用場景中發揮重要作用。本文將詳細介紹如何在Linux環境下部署安全可靠的FTP檔案服務,採用業界廣泛認可的vsftpd服務軟體,幫助您快速建構高效能的檔案傳輸平台。
在數位化浪潮中,一個高效穩定的網站如同企業的「數位門面」。當我們談及自主建站,WordPress憑藉其41%的全球市佔率,始終是開發者的首選方案。但隨著雲端技術演進,「如何在雲伺服器實現企業級WordPress部署」已成為值得深究的課題。

在全球化數位浪潮加速演進的今天,雲端計算服務已成為跨國企業和全球開發者構建數位化業務的核心基礎設施。作為亞太地區領先的雲端服務提供商,阿里雲國際站(Alibaba Cloud International)透過遍佈全球的資料中心和豐富的雲端產品矩陣,為來自200多個國家和地區的企業及開發者提供穩定可靠的雲端服務。

Alibaba has launched Qwen3, the latest generation of its open-sourced large language model (LLM) family, setting a new benchmark for AI innovation.

This article describes the core features of Spring AI Alibaba.

This artile introduces the usability and maintainability of EMR Serverless Spark in stream processing.

This article introduces how to integrate Microsoft Entra single sign-on (SSO) with Alibaba Cloud

This post is going to introduce Alibaba Cloud Key Management Service (KMS).

This article introduces XRPC, a technical solution that addresses complex communication requirements between compute nodes and data nodes in PolarDB-X.

This article discusses the process of online backup restoration and addresses three key questions regarding the recovery of database consistency.

This article focuses on building a Stable Diffusion API environment with Alibaba Cloud Function Compute.

This article focuses on using Terraform to quickly deploy Magento on Alibaba Cloud ECS + RDS.

This article focuses on deploying Magento on Alibaba Cloud Container Service for Kubernetes (ACK).
