Explore hidden costs of data breaches and learn key cybersecurity strategies to protect your business in the cloud era for long-term success.

This article walks you through the current challenges in cloud cybersecurity and strategies to effectively address them.

Sebagai security reseacher atau bug hunter, recon merupakan hal yang sangat penting dalam proses mencari celah keamanan atau bug.

This blog post shares the parallels of cybersecurity with epidemics and discusses the importance of cloud security operations for enterprises.

Trong kỷ nguyên số hiện đại, bảo mật thông tin trở thành một trong những ưu tiên hàng đầu cho các doanh nghiệp, đặc biệt là tại thị trường đang phát triển nhanh chóng như Việt Nam.

While Web3 emerges as the next significant evolution of the internet, it poses security challenges that demand immediate attention.

Zero-Day Resilience: Ransomware Defense with Cloud Firewall and Security Center Ransomware is a type of malicious program or malware that threatens vi.

Alibaba Cloud Independent Software Vendors (ISVs) is here to empower your digital transformation. In collaboration with industry-leading partners such.

In the realm of web security, the strategic deployment of a Web Application Firewall (WAF) stands as a pivotal measure to fortify the defense mechanis.

This article explores Alibaba Cloud's commitment to cybersecurity, examining its comprehensive suite of security tools, partnerships with industry lea...

Data is the lifeblood of the financial industry. 91% of financial companies worldwide think they have data security risks.
This article explores the concepts of Red Team and Blue Team in cybersecurity, describing their roles and activities in testing and improving an organization's security posture.

The article provides an overview of the concept of "dorks" in the field of cybersecurity.

Cloud Computing is at the heart of the Fourth Industrial Revolution (4IR) in which technology emerges as the key enabler within societies.

Data security has now become major concern for companies, organizations, government authorities, and even individuals alike.

Best Practices for a Global MNC Network Design with Fortinet Secured SD-WAN Solution Industry

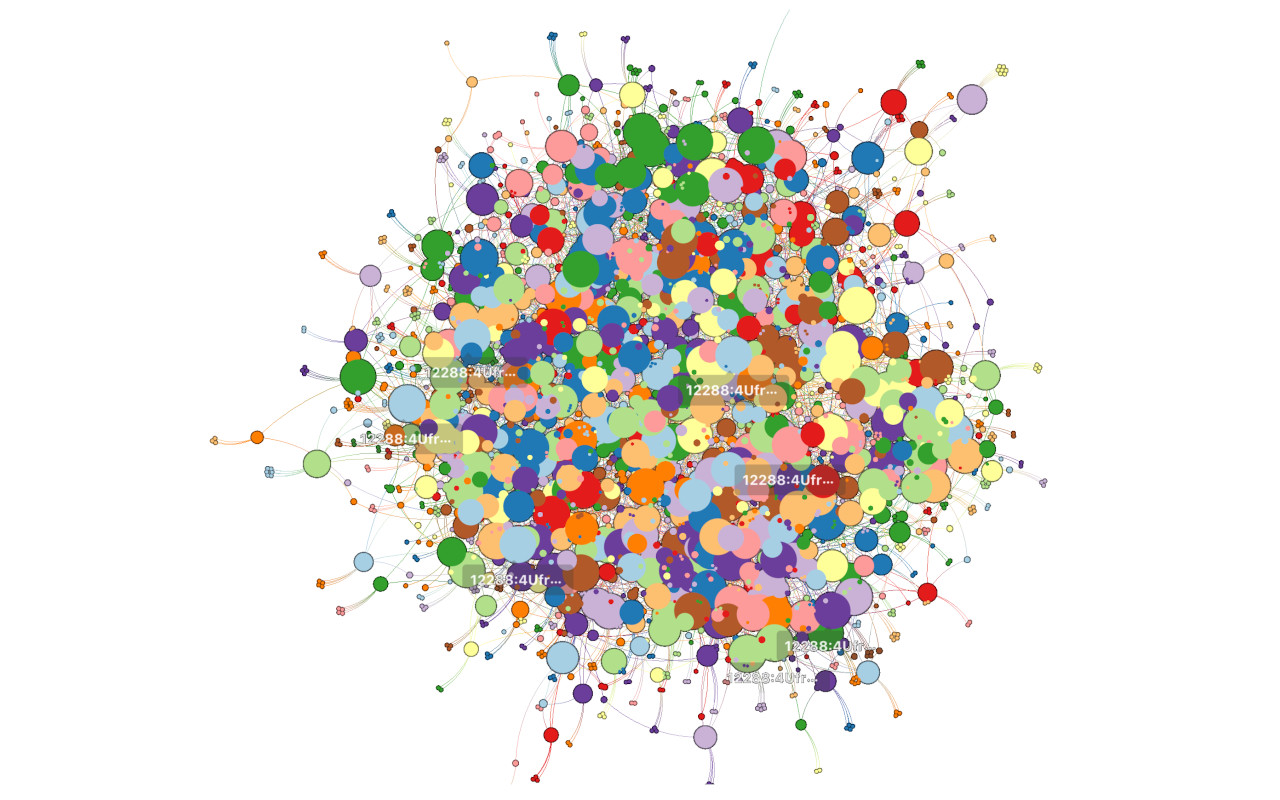
In this article, I describe how my team at Alibaba Cloud implemented fuzzy hashing at scale, showing visualizations of our XOR DDoS detection.
Protos Labs impressed the judges with its threat-based cyber risk quantification methodology and proactive cybersecurity services for the insurance industry.

Alibaba Cloud MVP Friday Five is a blog column to share interesting and helpful content brought by global Alibaba Cloud MVPs.

Alibaba Group chief security expert Xiao Li shares his insights on the trends of network security in the one, five, or even ten years may have profoun.
